API Authentication and Security: Best Practices for Securing Your APIs, Including Token-Based Authentication and OAuth
December 31, 2024
As APIs become more integrated into web applications, securing them is more important than ever. If your API exposes sensitive data or allows users to perform actions (like making payments), it’s essential to ensure that only authorized users can access it. In this blog, we’ll cover the best practices for securing your APIs, including token-based authentication and OAuth.
1. Token-Based Authentication (JWT)
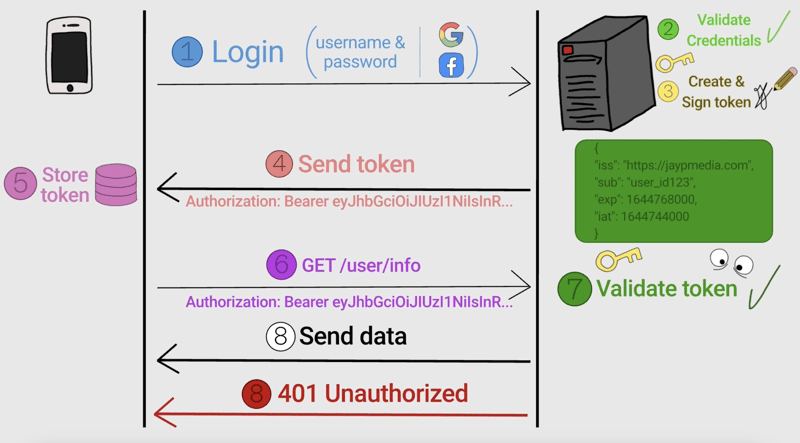
One of the most common ways to secure an API is through token-based authentication, often using JWT (JSON Web Tokens). JWT is a compact, URL-safe token format that securely transmits information between the client and server. The server issues a token upon successful login, and the client includes this token in subsequent requests to access protected routes.
How JWT Works:
- Login: The user logs in with their credentials, and the server returns a JWT.
- Authorization: The client stores the token (usually in localStorage or cookies) and sends it with each request in the
Authorizationheader. - Verification: The server verifies the token to ensure it is valid and not expired.
2. OAuth Authentication
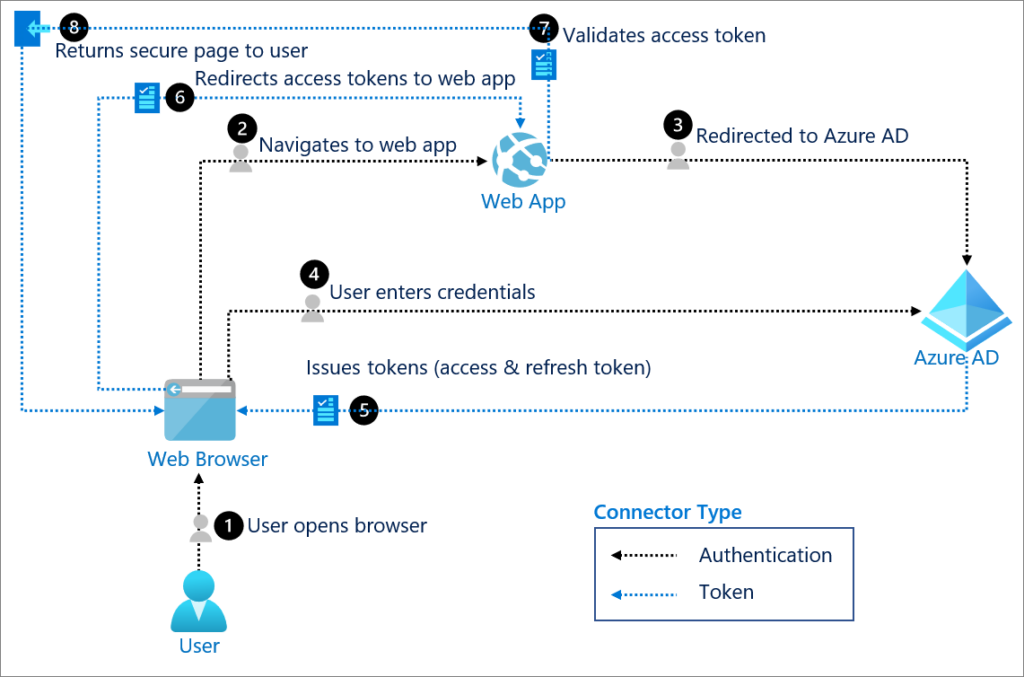
OAuth is a protocol that allows third-party applications to access user data without sharing login credentials. OAuth is often used for single sign-on (SSO) solutions, such as logging in with Google or Facebook.
OAuth Flow:
- Authorization Request: The user is redirected to an authorization server (e.g., Google) to grant permission.
- Access Token: Once the user authorizes, the authorization server issues an access token.
- Token Exchange: The client application exchanges the access token for an API response, allowing the app to access the user’s data securely.
3. Other API Security Best Practices
- Use HTTPS: Always ensure your API is served over HTTPS to encrypt the data in transit and prevent man-in-the-middle attacks.
- Rate Limiting: Implement rate limiting to prevent abuse by limiting the number of requests a client can make in a given period.
- IP Whitelisting: Restrict access to your API by allowing only trusted IPs to make requests.
- Scopes and Permissions: Use fine-grained access controls by defining scopes and permissions to restrict which data can be accessed.
Conclusion
Securing your APIs is a critical step in protecting your application and its users. By implementing token-based authentication (JWT), OAuth, and following other security best practices, you can safeguard your APIs and ensure that only authorized users have access.